While the world is in lockdown, it seems that online phishing attacks are on the rise. Now that everybody stays at home and people spend much more time online, online scams are skyrocketing and many people fall victim to them. Here’s a short guide on simple things to remember in order to stay safe from phishing attacks, while you’re staying safely at home.
But What Is Phishing/Online Scams?
Born circa 1995, just 4 years after the first site appeared, phishing refers to the practice of using deceptive emails and websites to illegally get personal and corporate information from users. That information – usernames, password, credit cards – is later used to steal either money or more information.
The word “phishing” itself is a combination of “fishing” and “phreaks” which was what hackers used to call themselves. The practice of phishing is considered a form of social engineering, which is a term for manipulating people by falsely representing oneself in the context of web security.
How Can You Protect Yourself From Phishing?
Because phishing can truly cost you a lot – from stolen money to huge data breaches in your company – taking proper safety precautions is a must. We’ve put together a shortlist of the things you need to keep in mind in order to stay safe online.
Pay Attention To The Sender And The URL In Your Emails
One of the most common phishing scams is to spoof a big brand by sending an email with their name (and usually color palette), and say there is something wrong with your account and ask you to log in “to fix it”. Usually, the look of the email is very similar to the original brand, however, there is a sure way to distinguish whether you’re looking at the real deal.
You need to check the email address: scammers cannot create email addresses with the actual domain name of the company, so instead of [email protected] it will usually look like [email protected] Look carefully at the email address and not just the name appearing in your email client!
Check URL
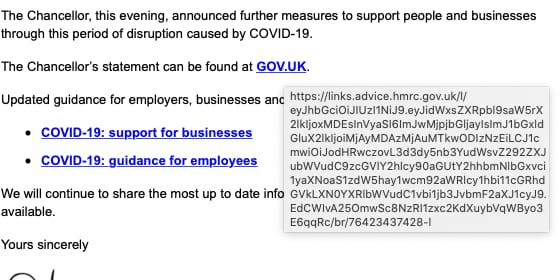
You should also check the URL before clicking. This can be done by hovering the mouse over the URL provided in the email, it will usually reveal the domain it’s pointing at, so you can see where this email actually wants to take you. If it’s not the official domain of the brand, don’t click on it.
Mouse over the link and the destination will show. Always check this if in doubt.
Avoid Downloading Email Attachments You Don’t Expect
Sometimes the email looks like legitime business emails, and they don’t pretend to be a big company, but instead send over an attachment containing some sort of malware. The email is often structured as a business offer or аn email sent by the recipient’s own company/management containing files with sensitive information.
If you don’t know who the sender is, definitely don’t open any attachments. If you know the sender, but you don’t expect anything from them, or there is something fishy about it, it’s better to be cautious. Call the sender and ask them if they meant to send you anything, as sometimes scammers hack into people’s email boxes and use them for phishing attacks by spamming their contacts.
The most common format for the attachments is zip (.exe is usually not allowed), however, even Microsoft Office files can contain viruses, which can contain macros that need to be enabled. Overall, keep an eye for all kinds of attachments.
Always Check The Domain You’ve Landed On
If you happen to click on a phishing link (usually via email or through instant messages), it will often take you to a website with a form of some sort. The purpose of these forms most often aim to gather your most sensitive information – usernames and passwords.
In order to be sure you’re at the correct site and before filling in any data, check the website address in the browser address bar.
Scammers can create a website closely resembling the design of the respective brand, but they can’t use their official domain or have the brand name in the domain (assuming the brand is trademark protected). So, often, these domains may resemble a brand’s name, but will never be the original one, and will have additional symbols, letters, or words.
Usually, the scammy domains look completely nonsensical and sometimes the design and flow also feels odd, especially if it’s a known brand that you often see.
For example, when signing into Gmail, Google will never ask you to select your email provider or enter both your email and password on the same screen. So the flow you will often see on phishing sites is designed to resemble the original one, but it’s not.
We have seen a large number or fake email pretending to Microsoft Office 365 account messages claiming payment has failed or security is compromised requesting you to log on.
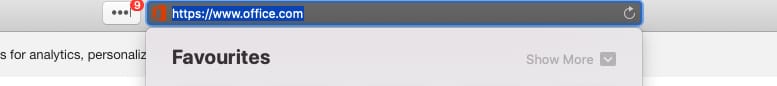
In safari just mouse over the URL in the address bar and the whole of the domain will be displayed.
Ignore Money Requests
Another type of online scam that social engineers often use is misrepresenting themselves and asking for money under some form. Usually, it’s a person in trouble, asking for financial help; you’re asked to send a small amount of money with the promise you’ll get way more in return.
Sometimes these scams can take the form of extortion. A popular one was an email circulating in the past couple of years, stating that users have been recorded through their own webcams watching adult content and asking for money. Actually, this scam attack was so scary, it made the news as people were terrified – understandably so!
Either way, if you are getting a money request under any form by strangers, it’s usually a scam; never give out money or financial information no matter how the situation is presented.
Remember, all the scammers need is just an email address in order to do some serious damage! Мindful internet usage is key to protecting your privacy and wellbeing on the web.
One more thing
One last thing an Apple MAC is safer than Windows. Don’t use Windows 7 or XP as they are not supported and have had no security updates for some time.
A mobile device is usually safer than a computer as they are less prone to running hidden scripts. Again an Apple mobile is inherently more secure than an Android phone where security is harder to implement due to the openness of the platform for 3rd party app developers and the wide variety of Android version in existence.
Stay safe and vigilant, while staying and working from home, and always guard your online data.
About us and this blog
We are a digital marketing company with a focus on helping our customers achieve great results across several key areas.
Request a free quote
We offer professional SEO services that help websites increase their organic search score drastically in order to compete for the highest rankings even when it comes to highly competitive keywords.